From Breaches to Bitcoin - Trading Stolen Cards on Jokerstash
In the shadows of the internet, a thriving black market once existed where stolen financial data was the most valuable currency. At the heart of this underground economy stood JokerStash—a notorious dark web marketplace that turned stolen credit cards into digital commodities. It acted as a global hub, connecting data thieves to fraudsters through an ecosystem powered by data breaches and cryptocurrency.
This article explores how jokerstash operated, how it facilitated the large-scale trade in stolen payment cards, and what made it a blueprint for modern cybercrime marketplaces.
🕵️ What Was JokerStash?
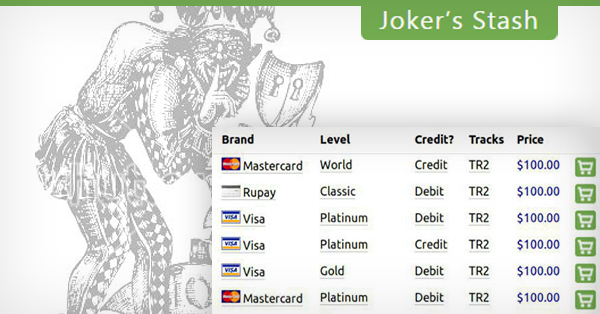
JokerStash (often written as Joker’s Stash) was a dark web carding marketplace active from approximately 2014 to 2021. It offered a wide array of stolen financial data, including:
-
Credit card dumps (Track 1 & Track 2 data)
-
CVVs (card-not-present data)
-
Fullz (full identity packages with SSNs, DOBs, and more)
-
Online banking credentials
-
Access to cryptocurrency wallets and prepaid accounts
JokerStash distinguished itself from other platforms with its reliability, volume of data, and global reach. It served as a middleman between hackers who obtained card data through breaches, and cybercriminals who monetized it through fraudulent transactions.
🏦 Step 1: The Breach – How Card Data Was Sourced
The journey from breach to trade began with the theft of data. Card details listed on JokerStash often came from:
-
POS malware on retail store payment terminals
-
Phishing campaigns targeting banks or individuals
-
Database hacks of e-commerce platforms
-
Skimming devices installed on ATMs or gas pumps
Major data leaks were branded with marketing-style names—like “TrumpDump”, “BigBadaboom”, or “BlazingSun”—and would appear on JokerStash shortly after the breach occurred (and often before it was publicly disclosed).
One of the platform's biggest drops came from the Wawa data breach (2019), which exposed over 30 million credit and debit card records.
💳 Step 2: Listing and Categorizing Stolen Cards
Once stolen, the card data was uploaded and organized on JokerStash’s platform. The site offered search filters similar to any legitimate e-commerce store. Buyers could sort cards by:
-
Country of issuance
-
Bank Identification Number (BIN)
-
Card type (Visa, MasterCard, AmEx)
-
Estimated balance or transaction activity
-
Freshness (newly breached data carried a premium)
This made it easy for fraudsters to buy region-specific cards, enabling targeted attacks based on location and spending behavior.
🛒 Step 3: Buying with Bitcoin and Monero
JokerStash required all transactions to be made using cryptocurrency, initially Bitcoin and later also Monero (XMR) for added privacy. Here’s how it worked:
-
Buyers registered anonymously on the platform.
-
They funded an internal wallet using crypto.
-
They browsed listings and made purchases instantly.
-
Card data was delivered via encrypted download.
Cryptocurrency allowed JokerStash to process global transactions quickly and anonymously, bypassing banking systems and avoiding detection.
🛠️ Tools That Enabled Fraud at Scale
To further professionalize card trading, JokerStash included features that mimicked legitimate fintech platforms:
✔️ Card Checkers
Buyers could test cards in real time to confirm they were still active before finalizing a purchase.
📊 Vendor Reputation
Though JokerStash was primarily a single-vendor platform (run by the admin known as “JokerStash”), some resellers had their own listings, complete with user reviews and feedback scores.
🧩 Campaign Branding
Each breach or dataset was marketed as a “drop,” complete with a name, description, and expiration date—creating hype and urgency, just like a limited-edition product launch.
🌍 A Global Financial Fraud Network
What made JokerStash so dangerous wasn’t just the data—it was the accessibility. The platform allowed anyone with cryptocurrency and basic technical knowledge to:
-
Buy a list of stolen cards from a major U.S. bank
-
Use that data for online purchases or ATM fraud
-
Resell the data on smaller forums or encrypted messaging groups
-
Launder the profits via crypto mixers or prepaid gift cards
This created a global ecosystem of fraud, enabling cybercrime to scale like never before. JokerStash was particularly favored by:
-
Carders (those who use cloned or stolen card data)
-
Drop service operators (who receive and redirect fraudulently bought goods)
-
Money launderers and cash-out crews
🧠 JokerStash's Impact on Dark Web Trade
JokerStash wasn't the first carding site—but it was the most influential. Here’s why:
🔒 1. Operational Longevity
Many dark web sites are taken down quickly. JokerStash lasted over 6 years, a rarity in the cybercriminal world.
💹 2. Market Standardization
It created pricing models and quality benchmarks for stolen data, much like a stock exchange sets value based on supply and demand.
📈 3. Scalable Fraud Infrastructure
Its tools, automation, and global reach turned small-time fraud into a scalable, semi-professional business model.
🧨 The Shutdown: End of an Era
In January 2021, JokerStash posted a farewell message stating:
“It’s time for us to leave forever. We will never ever open again.”
The closure came amid a wave of law enforcement operations targeting dark web markets, as well as increasing pressure from blockchain analysis companies and global financial crime units.
Though no arrests were publicly announced, many speculate the operators retired with considerable crypto wealth—or were warned of imminent seizure.
🛡️ How to Protect Yourself from Data Trading Markets
Even though JokerStash is gone, similar marketplaces still exist. Protect yourself with these steps:
-
Use unique, strong passwords for every account
-
Enable multi-factor authentication
-
Monitor your credit report and bank statements
-
Sign up for data breach alerts at jokerstashh
-
Avoid using public Wi-Fi for sensitive logins
-
Consider a credit freeze if you suspect identity theft
🔚 Final Thoughts
JokerStash created a global black market powered by data breaches and Bitcoin. It industrialized credit card fraud by connecting hackers, buyers, and launderers in a seamless, anonymous supply chain. The result was a new kind of global trade—one that didn’t involve stocks or commodities, but your financial identity.
Its legacy continues in successor platforms and Telegram-based shops, reminding us that in the digital age, information is both currency and commodity—especially when it’s stolen.